Decoding LAN Communication: How Data Travels in Your Local Network
Computer Networking Fundamentals, data collision, Carrier Sensing, Collision Detection, Polling Method
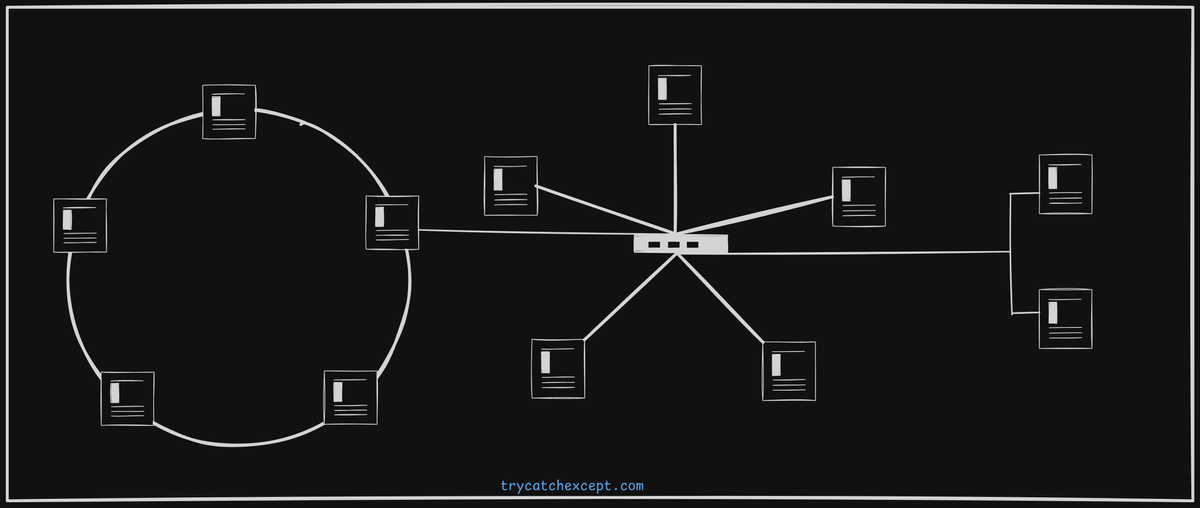
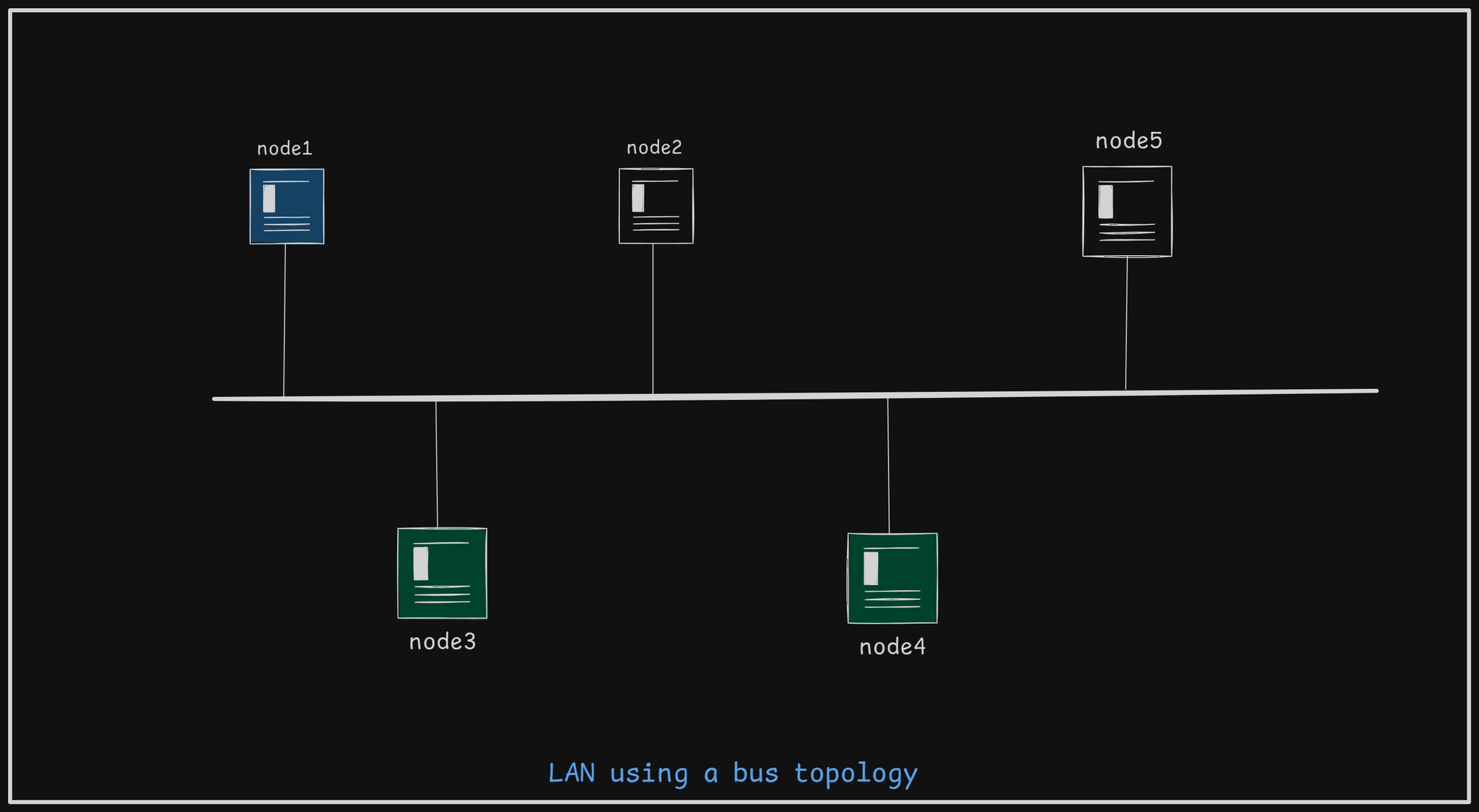
In a basic network using a bus topology, as shown in the image below, let's examine what occurs when different nodes attempt to communicate with each other. We'll explore the challenges that arise, such as potential collisions, and the core techniques used to manage them, like collision detection and carrier sensing.
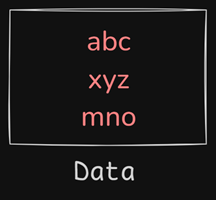
Data and Medium
If node1 wants to send data to node5, it will put the the data onto the shared medium while data travels through the medium and reaches the node5.
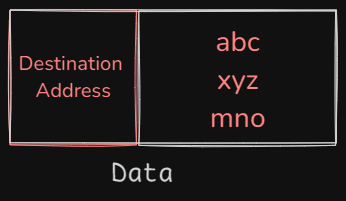
node2, node3 and node4.Data along with address and Medium
To ensure the data reaches only the intended recipient node5, the sender node1 includes the destination node5 system's address in the header of the transmitted data.
The receiving nodes use this address to check if the address in the incoming header matches their own. If it matches, they process the data; otherwise, they simply ignore it.
Data Collision - now there could be more than one node transmitting the data as medium is common accross all the nodes. Data from two different nodes may mixed up and result data collision.Carrier Sensing
When node1 is transmitting data to node5, but node2 begins sending data at the same time. This can lead to a collision on the network. To minimize this risk, the Carrier Sensing technique is employed.
How it works:
- A device "senses" the carrier signal (the signal indicating an active transmission) on the network before attempting to transmit.
- If no carrier signal is detected (medium is idle), the device starts transmitting data.
- if a carrier signal is detected (medium is busy), the device waits until the medium becomes idle before attempting to transmit again.
It reduces the chances of collisions and improving overall network efficiency.
Random access method with Collision Detection
When both node1 and node2 attempt to send data to node5 simultaneously and both find that medium is idle, it can still lead to a collision on the network. Random Access Methods (RAMs) are protocol that allow mulitple devices on a network to share a common communication medium.
Collision Detection Process:
- Carrier Sensing
- Simultaneous Transmission
- Collision Detection: While transmitting, the device also monitors it's receieved signal for any interference. If it detects a collision, it immediately stops transmitting.
- Backoff and Retransmission: After a collision, the device waits for a random amount of the time before attempting to retransmit. This random backoff helps to reduce the likelihood of another collision.
Bus Starvation, where the systems that collided struggle to regain access while others find the carrier available first.Polling Method
In the Polling method, instead of devices trying to talk to each other whenever they want, the network takes turns like a classroom where only one student speaks at a time.
Here’s how it works:
-
The Controller: One device is chosen to be the "teacher" or controller of the network. This teacher is in charge of giving permission to the other devices to send their messages.
-
The Token: The teacher gives out a special "token" (like a speaking pass) to each device in a specific order, one after the other. Only the device with the token is allowed to send its message.
-
No Talking Over Each Other: Since there is only one token and only one device can talk at a time, there won’t be any overlapping or confusion—no collisions happen.
So, in this system, devices wait for their turn to talk, making communication smooth and organized!
Takeaways
- Addressing Data: Each data packet has an address so that it reaches the right device in the network.
- Data Collisions: Sometimes, multiple devices try to send data at once, causing confusion or collisions.
- Carrier Sensing: Devices listen to the network first to check if it's clear before sending their data, helping to avoid collisions.
- Role of RAM: RAM helps store data temporarily, ensuring smooth communication between devices.
- Polling Technique: A controller gives permission for devices to talk one at a time, preventing collisions and making sure everyone gets a turn.
These techniques make sure that data travels efficiently and correctly in a local network.
💡Your next reading topic.