Exploring the OSI Model: The Foundation of Modern Networking
The OSI (Open Systems Interconnection) Reference Model is a seven-layer framework developed by the ISO in the late 1970s. It standardizes telecommunication and computing functions, enabling diverse networking protocols to communicate seamlessly. Understanding the OSI model is essential for network engineers and IT professionals, as it forms the basis of modern networking. 🌐📡✨
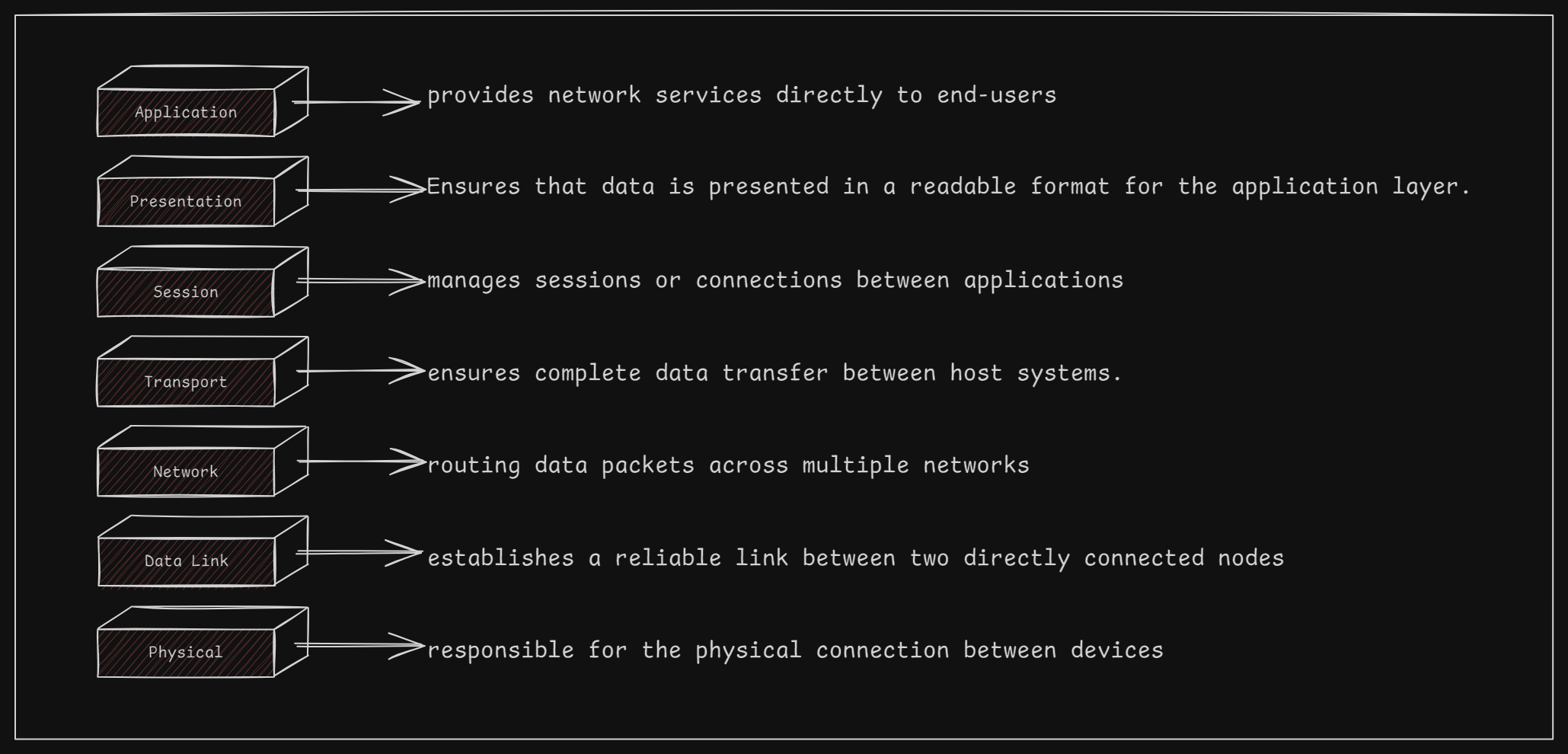
Physical Layer (Layer 1)
It is unique among the OSI model's layers because it is the only one that physically transmits data across the network interface. While the other layers work to create and prepare messages, the data must ultimately be passed down to the physical layer for actual transmission over the network.

Physical Layer Functions 🌐🔌
-
Hardware Specifications
The physical layer defines how the hardware operates, including cables, connectors, wireless radios, and network interface cards (NICs). It's all about the physical devices that make networking possible. -
Encoding and Signaling
This layer takes data (bits) from your device and transforms it into signals that can travel across the network. It uses the right modulation techniques to send the data efficiently. -
Data Transmission & Reception
Once the data is encoded, the physical layer is responsible for actually transmitting it across the network. This applies to both wired and wireless networks—whether there's a physical cable or not, the data still travels through this layer. -
Topology & Physical Network Design
The physical layer also handles the layout of your network, including things like LAN and WAN topology. However, the physical layer can’t be fully separated from the data link layer. For instance, Ethernet cables are part of the physical layer, but their maximum length is influenced by rules defined in the data link layer. So, even though the physical layer focuses on hardware, it's always closely tied to the layer above it.
Data Link Layer (Layer 2)
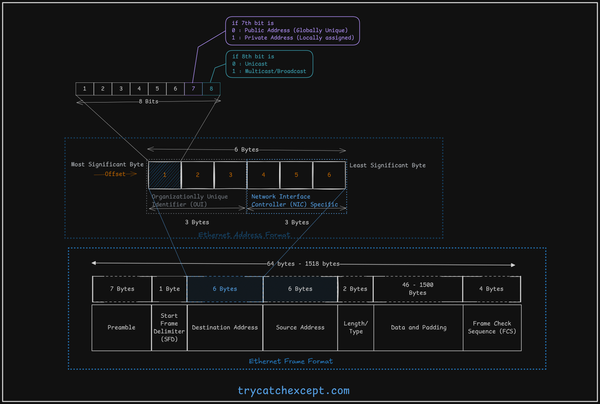
The data link layer, also known as layer 2 in the OSI model, enables systems to communicate on the same network, whether wired or wireless. This layer powers technologies like Ethernet, Wi-Fi (802.11), and Token Ring, which are key for local area networks (LANs).

It's further divided into two sublayers:
- Logical Link Control (LLC): Manages communication between devices.
- Media Access Control (MAC): Controls how devices gain access to the network and permission to transmit data.
By splitting these roles, different network technologies can work together more seamlessly, making it easier to integrate various systems.
Key Functions of the Data Link Layer (Layer 2)
-
Logical Link Control (LLC):
- Establishes and manages logical connections between devices on a local network.
- Hides data link layer details from higher layers to enable seamless communication.
- Common protocol: IEEE 802.2 LLC.
-
Media Access Control (MAC):
- Controls access to the shared network medium (e.g., cables).
- Prevents conflicts by following specific rules like:
- CSMA/CD (Ethernet) – detects collisions and resends data.
- Token Passing (Token Ring) – passes a token to regulate data transmission.
-
Data Framing:
- Encapsulates higher-level data into frames for transmission.
- Adds source/destination addresses in the header and error detection in the trailer.
-
Addressing:
- Assigns unique hardware addresses (MAC addresses) to devices for identification.
- Ensures data reaches the correct device on the network.
-
Error Detection and Handling:
- Detects and handles errors using methods like Cyclic Redundancy Check (CRC).
- Ensures data integrity during transmission.
-
Physical Layer Relationship:
- Works closely with the physical layer; for instance, Ethernet (IEEE 802.3) specifies both data link and physical layer standards.
- Network devices like NICs (Network Interface Cards) and switches operate at this layer, making decisions based on frame data.
-
Technologies and Protocols:
- Popular layer 2 technologies include Ethernet, Token Ring, IEEE 802.11 (Wi-Fi), and protocols like PPP and SLIP for serial communication.
Network Layer (Layer 3)
While the data link layer manages communication between local devices, the network layer ensures data reaches devices on different networks, often referred to as internetworks.
This layer is crucial for enabling communication between different networks, ensuring that data finds its way across complex paths, all while managing packet size and addressing issues.
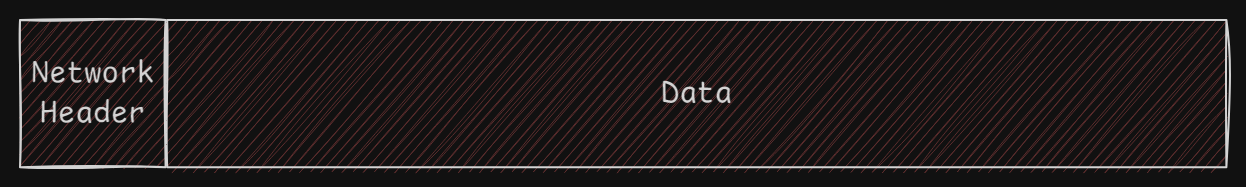
Key Functions of the Network Layer:
-
Logical Addressing:
- Assigns unique logical addresses (like IP addresses) to devices.
- Unlike physical addresses (MAC) used by the data link layer, these logical addresses are independent of hardware and allow devices to communicate across different networks.
-
Routing:
- Defines the path for data to travel across multiple interconnected networks.
- Devices like routers use logical addresses to determine the best path for data to reach its destination.
-
Datagram Encapsulation:
- Encapsulates data into datagrams (or packets) by adding a network layer header before passing them down to the data link layer.
-
Fragmentation and Reassembly:
- If data packets are too large for the data link layer, the network layer fragments them into smaller pieces.
- Once they arrive at the destination, the packets are reassembled.
-
Error Handling and Diagnostics:
- Utilizes protocols to exchange information about network health, helping with diagnostics and error resolution between devices and routers.
Transport Layer (Layer 4)
The transport layer sits in the middle of the OSI model and bridges the gap between the lower layers (responsible for moving data) and the higher layers (focused on applications).
It ensures smooth communication between software applications on different devices, without worrying about how the data is physically moved.

Key Functions of the Transport Layer
-
Process-Level Addressing (Port Addressing):
- Differentiates between software programs using port numbers, enabling multiple applications to use the network layer simultaneously.
-
Multiplexing and De-multiplexing:
- Multiplexing: Combines data from multiple applications into a single stream for transmission.
- De-multiplexing: Separates incoming data streams and directs each portion to the appropriate application.
-
Segmentation, Packaging, and Reassembly:
- Segmentation: Splits large data into smaller pieces for transmission.
- Reassembly: Combines segmented pieces back into the original data on the destination machine.
-
Connection Management:
- Handles both connection-oriented and connection-less communications.
- Manages the entire lifecycle of a connection: establishment, maintenance, and termination.
-
Acknowledgments and Retransmissions:
- Ensures reliable delivery by using acknowledgments to confirm data receipt.
- If no acknowledgment is received, the data is retransmitted.
-
Flow Control:
- Regulates data transmission speed to prevent overwhelming the receiver, especially when there's a speed mismatch between sender and receiver.
-
Error Control:
- Detects and corrects errors before delivering data to applications using checksums and retransmission requests if necessary.
-
Sequencing:
- Ensures that out-of-order packets are arranged in the correct order before passing them to the application.
Relationship Between Transport Layer and Network Layer 🌐
-
Close Connection:
- Though theoretically distinct, the transport and network layers are closely related in practice.
- Common protocol suites, like TCP/IP, highlight this connection by naming them after both layers (TCP for transport, IP for network).
-
Host-to-Host vs. End-to-End Communication:
- The network layer enables communication between computers on different networks (host-to-host).
- The transport layer allows communication between applications on different systems (end-to-end).
-
Complementary Roles:
- The network layer identifies the network and computer on that network.
- The transport layer identifies the specific application on that computer.
-
Interdependence:
- Without the network layer, the transport layer wouldn’t know which system to send data to.
- Without the transport layer, it wouldn’t matter if data reached the destination computer since there would be no way to deliver it to the correct application.
Therefore, both layers depend on each other for complete communication.
Session Layer (Layer 5)
It is the fifth layer and the first of the upper three layers focused on software application processes rather than data delivery or network details.
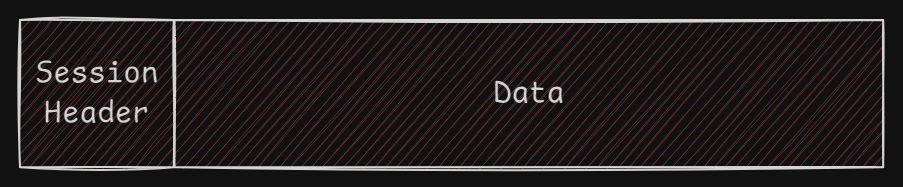
Key Functions of the Session Layer
-
Establishing and Managing Sessions:
- Its primary role is to establish, manage, and terminate sessions between two software applications, like a persistent link allowing them to exchange data for an extended time.
- A session is like a telephone call, maintaining communication between two parties for ongoing interactions.
-
Enhanced Services Beyond Data Transport:
- Dialogue Control: Determines whether data can flow in both directions simultaneously or one direction at a time, ensuring proper data exchange flow.
- Token Management: Controls which party can perform critical tasks at a given time, avoiding conflicts by using tokens.
- Synchronization: Allows setting checkpoints during data transfers (like a large file transfer), so in case of a crash, only data after the last checkpoint needs to be retransmitted.
-
Application Program Interfaces (APIs):
- The session layer provides APIs (like NetBIOS, Sockets, and Remote Procedure Calls (RPCs)) to help higher layers set up and manage sessions.
- APIs enable application developers to easily create software that can communicate over networks, like TCP/IP, without needing to know the lower-level details of these protocols.
- For example, Sockets is a widely used API in both UNIX and Windows, allowing programmers to create Internet-capable applications.
Presentation Layer (Layer 6)
It is the sixth layer of the OSI Model, right below the top (Application Layer).
It has a more specific and limited function compared to other layers. Not always necessary; many connections can skip this layer.
It handles the formatting and presentation of data between systems, ensuring data can be interpreted correctly by different machines. It takes care of any special processing of data before sending it over the network.

Key Functions of the Presentation Layer
- Translation: Ensures different types of computers (PCs, Macs, UNIX systems) can understand each other by hiding differences in data representation.
- Compression: Compresses data to improve throughput, e.g., zipping/unzipping files.
- Encryption: Handles some encryption/decryption to secure data during transmission.
Optional Use:
The layer's functions (translation, compression, encryption) aren't always
required, which is why it's sometimes skipped.
In some cases, application layer protocols may directly handle these tasks, or > they may communicate directly with the session layer (Layer 5).
Application Layer (Layer 7)
It is the topmost layer of the OSI Model and handles network applications that interact directly with the network to perform tasks like browsing the web or sending emails.
Key Points:
- The application layer provides services that are used by user applications, but the actual software (e.g., browsers, email clients) doesn’t fully reside in this layer. Instead, they rely on protocols like HTTP for web browsing or SMTP for email.
- Not all applications use this layer directly. For example, a text editor opening a file over the network is managed by the operating system, not the application layer.
- Some operating systems also interact with the application layer directly, using its services to manage network-related tasks.
Responsibilities:
- The application layer provides services to programs and users who want to interact with the network.
- It doesn’t serve any layer above it, as it’s the topmost layer, but instead coordinates the use of lower layers to enable network-based tasks like email, web browsing, or messaging apps.
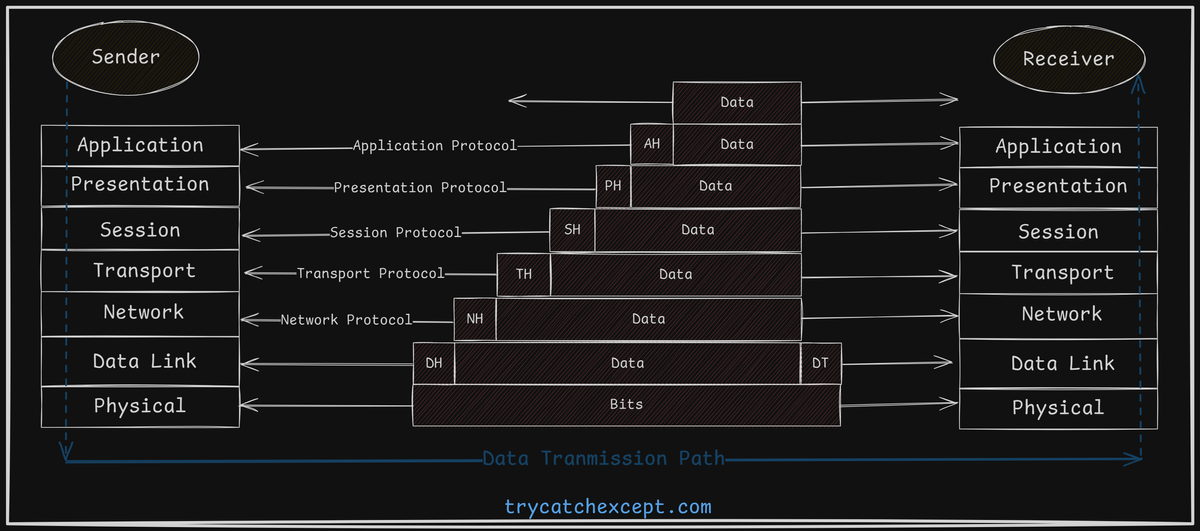
How data communication takesplace in OSI Model?
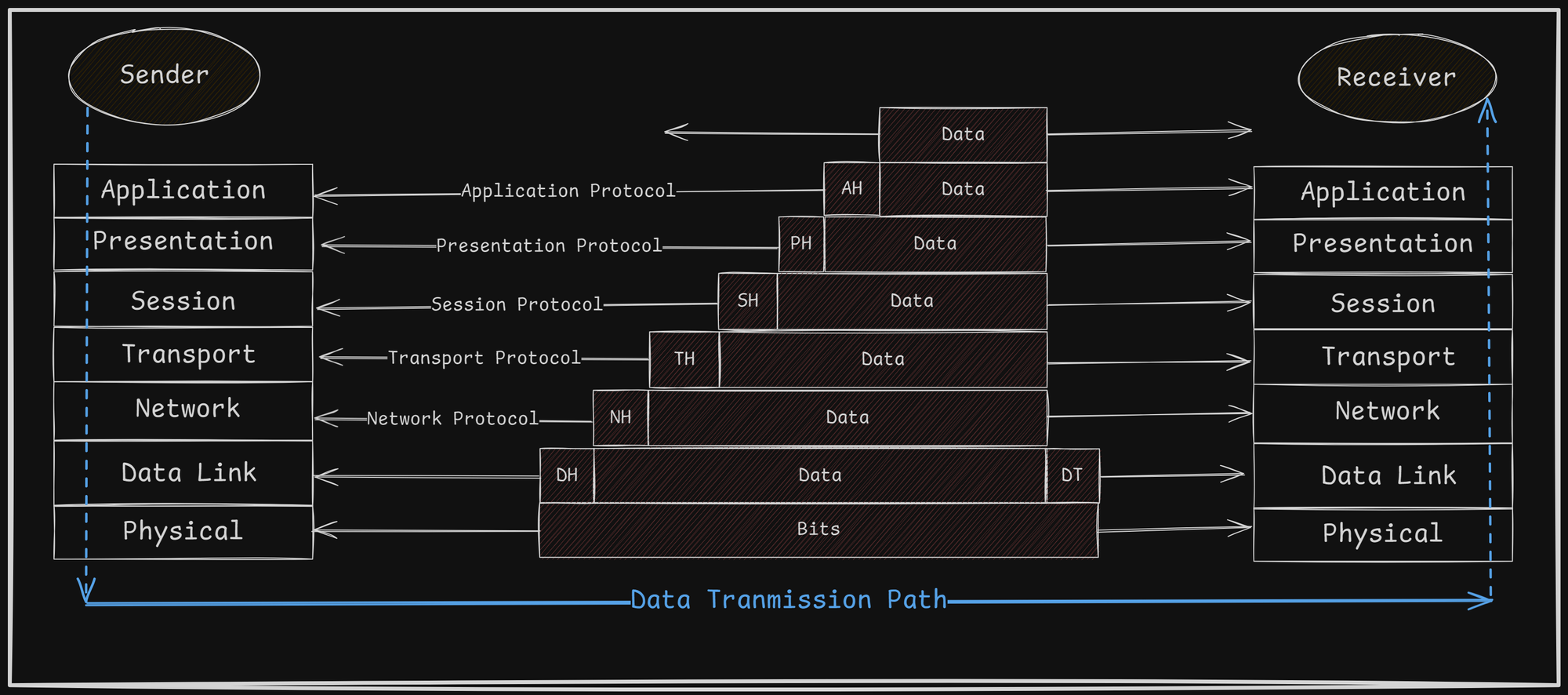
-
User Interaction:
- Communication begins when a user interacts with an application (e.g., Google Chrome) at the application layer.
- The data provided by the user is passed down through each layer of the OSI model, where headers are added to ensure proper transmission and processing.
-
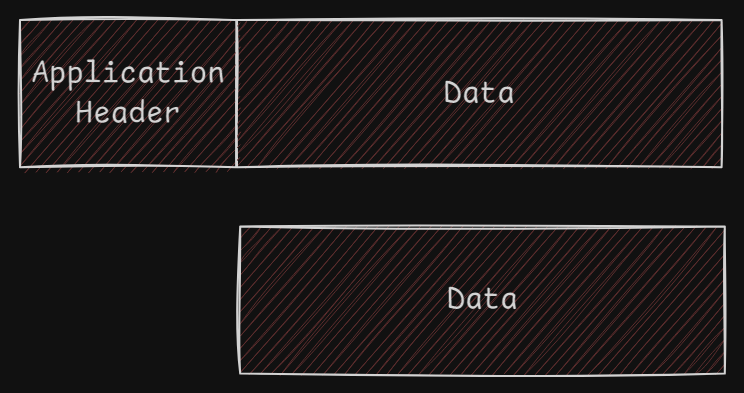
Layer-by-Layer Encapsulation:
- The Application Layer adds an Application Header (AH), which helps the receiving system process the data.
- The Presentation Layer adds a Presentation Header (PH), ensuring that the data format and syntax are correct.
- Session, Transport, and Network Layers each add their respective headers for managing sessions, end-to-end communication, and network routing.
- The Data Link Layer adds a Data Link Header and a trailer to create a frame. This includes the destination's hardware address and error-checking information.
- The Physical Layer converts the data into voltage levels that represent logical high and low values for transmission over the physical medium.
-
Data Encapsulation:
- As the data moves down the OSI layers, each layer adds its own header, a process called data encapsulation. This ensures that the corresponding layer at the receiving end can process the information correctly.
-
Transmission Over Physical Media:
- The data, now a series of electrical signals, travels over the physical medium to the receiving device.
-
Receiving and De-capsulation:
- At the receiving end, the Physical Layer interprets the signals and passes them to the Data Link Layer, which checks the hardware address and verifies the error-checking trailer.
- Each layer then removes its corresponding header (a process called data de-capsulation) and passes the remaining data to the next higher layer.
- Finally, the Application Layer delivers the data to the correct user application.