Networking Simplified: Understanding the Layered Model
Layered approach to networking, ISO-OSI reference model, The OSI Reference Model, Network Architecture, Protocol Stack
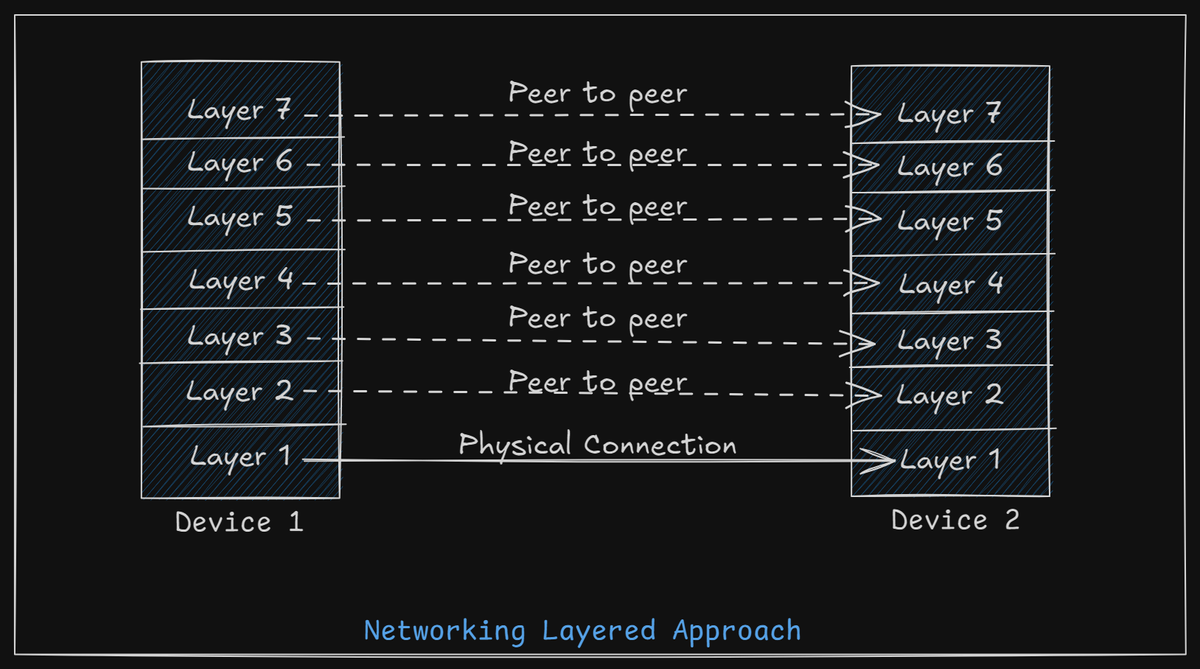
Computer networks are a mix of hardware and software, and to manage their complexity, they are designed in layers. Each layer builds on the one below it, offering services to the higher layers while hiding the technical details of how those services work. This layered design makes networks easier to manage and more efficient.
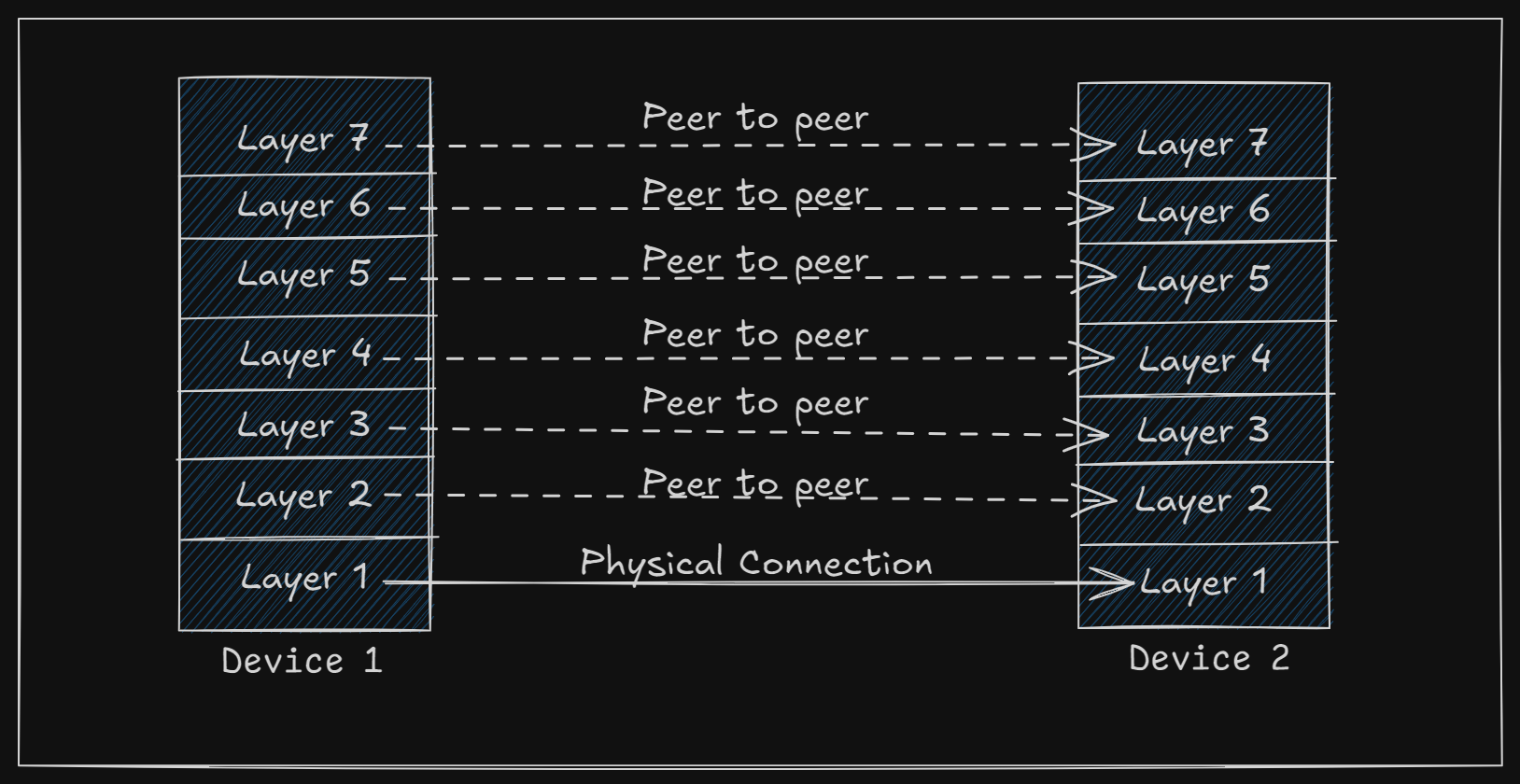
In a network, each layer on one computer communicates with the same layer on another computer using a set of agreed-upon rules, called protocols. These "peers" (which could be software, hardware, or even people) communicate following these protocols.
In reality, data doesn’t move directly from one layer on one machine to the same layer on another. Instead, it passes through each layer, one by one, down to the physical layer, which is responsible for the actual transmission of data over a physical medium (like a cable or wireless signal).
This organization of layers and protocols is referred to as network architecture, while a specific set of protocols used by a given system one protocol for each layer is known as a protocol stack.
Key Issues to Address in Network Layers
-
Addressing and Identification: Every layer requires a way to identify both the sender and receiver. With multiple devices and processes in a network, a clear addressing system is needed to specify the exact destination of data.
-
Data Transfer Rules: Data flow can be one-way or two-way depending on the system. Some protocols support multiple channels, with different priorities (e.g., one for regular data, one for urgent data). This is known as duplex control.
-
Error Control: Communication circuits can encounter errors, so error detection and correction methods are essential. Both sender and receiver must agree on how errors are handled. The receiver must acknowledge whether a message was received correctly or not.
-
Message Ordering: In some networks, messages may arrive out of order. To address this, protocols use sequencing, where data packets are numbered so they can be reassembled in the correct order.
-
Flow Control: Flow control is used to prevent a fast sender from overwhelming a slower receiver. This can be done through feedback from the receiver or by limiting the sender's transmission rate.
-
Fragmentation and Re-assembly: Some processes can't handle long messages, so messages need to be split (fragmented), transmitted, and then reassembled at the destination. Similarly, sending very small units of data can be inefficient, so multiple small messages are combined into a larger one and then split (dismembered) again at the receiving end.
-
Multiplexing and De-multiplexing: Setting up a separate connection for each communication can be expensive or impractical. To solve this, multiple conversations can share the same connection (multiplexing), and at the destination, they are separated (de-multiplexing). Multiplexing is particularly useful at the physical layer, where different connections share a few physical circuits.
-
Routing: When there are multiple paths between a source and destination, a decision is needed on which path to use. High-level decisions may depend on factors like privacy laws (e.g., sending data through France or Germany), while low-level decisions might depend on current network traffic.
-
Connection-Oriented vs. Connectionless Services:
- Connection-Oriented Service: Similar to how the telephone system works. A connection is first established, data is sent, and then the connection is released. Usually, data arrives in the same order it was sent. Parameters like message size and quality of service are often negotiated at the start.
- Connectionless Service: No need to establish a connection; each data packet is sent individually and may take different paths, with no guarantee of order.
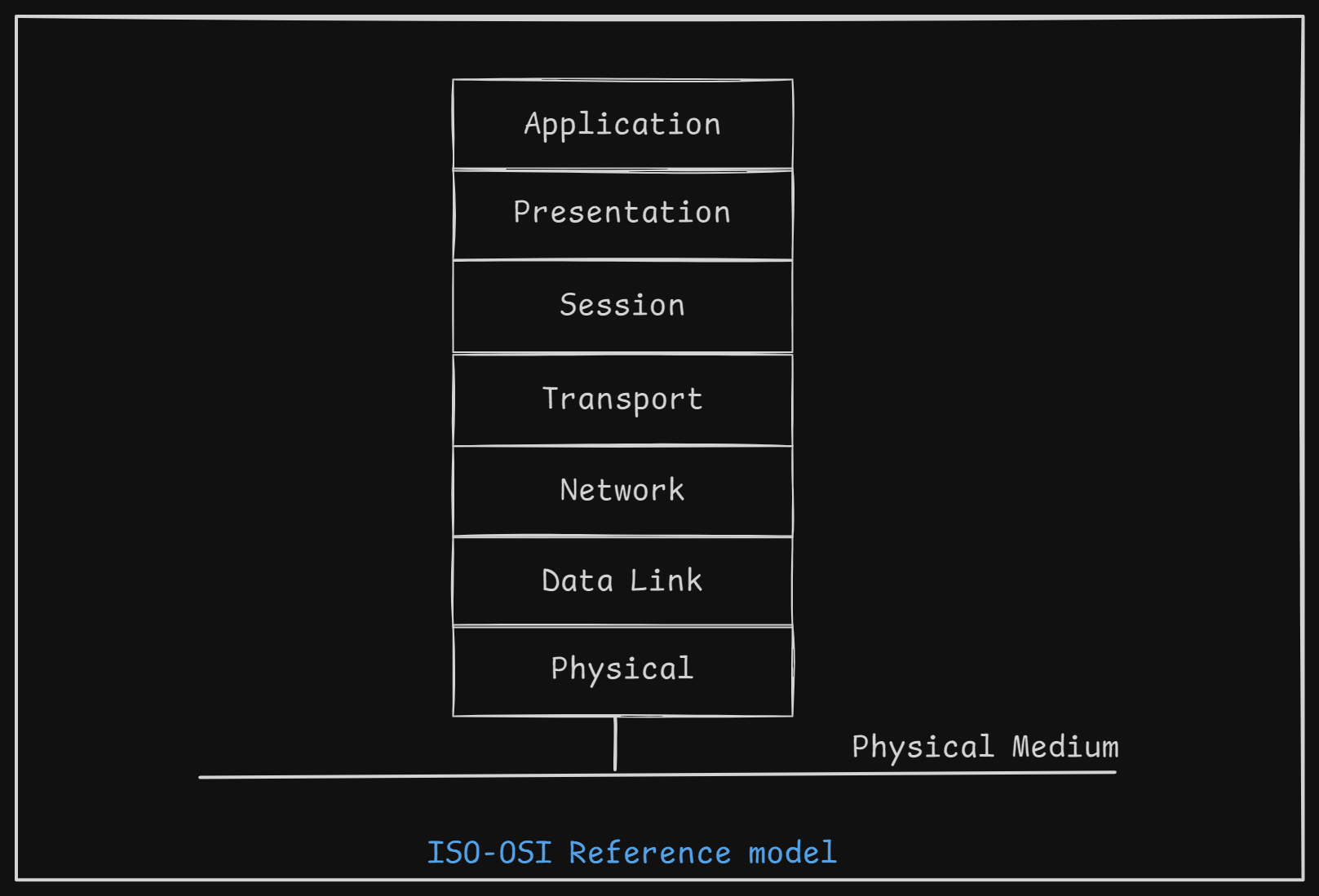
The ISO-OSI reference Model
-
Purpose of the OSI Model:
Initially aimed to create a unified framework to help hardware and software manufacturers develop networking technologies that work together seamlessly. -
Origins:
- In the late 1970s, two independent projects started with the same goal of defining a standard for networking.
- One project was led by the International Organization for Standardization (ISO), and the other by the International Telegraph and Telephone Consultative Committee (CCITT).
-
Merging of Standards:
- By 1983, these two organizations combined their efforts, producing a single, unified standard known as The Basic Reference Model for Open Systems Interconnection.
- It’s more commonly referred to as the OSI Reference Model, or just the OSI Model.
-
Publication:
In 1984, this model became an official standard:- ISO: Published as ISO 7498.
- CCITT (now ITU-T): Published as X.200.
-
Educational Use:
Though the OSI Model is often viewed as an educational tool today, its original purpose was to create a practical framework for developing networking technologies. -
Intended Role of OSI Model:
- The OSI Model was supposed to be the foundation for a universal set of protocols called the OSI Protocol Suite.
- The idea was to create a common system for global networks (similar to what the
internetbecame).
-
Competition with TCP/IP:
- The rise of the Internet and its TCP/IP protocols challenged the OSI Protocol Suite.
- In the end, TCP/IP won out, becoming the standard for internet communications.
- Some OSI protocols were used, but the suite as a whole didn't succeed.
-
OSI Model's Shift in Purpose:
- Even though the OSI protocols weren't widely adopted, the OSI Model itself became an important tool for explaining how networking works in general.
- It became widely used for education and to describe how different protocols, devices, and software interact with each other.
-
Uses of the OSI Model:
- It helps describe how different networking technologies fit into its seven layers.
- This includes things like networking protocols, software applications, and hardware devices such as switches and routers.
- It's also helpful for developers of software and hardware by clarifying the roles of each part in a networking system.
| Aspect | OSI Model | Current Internet (TCP/IP) |
|---|---|---|
| Purpose | Conceptual framework for networking | Actual protocol suite used on the Internet |
| Layers | 7 layers to explain networking operations | 4 layers (Link, Internet, Transport, Application) |
| Success | Widely used as an educational tool | Became the global standard for internet communications |
| Protocol Examples | Describes various protocols, but doesn’t define them | TCP, IP, HTTP, FTP, DNS |
| Adoption | Conceptual, not for direct use | Universally adopted for the Internet |
Key Benefits of the OSI Model:
- Simplifies Networking: Helps users understand the overall structure of networking.
- Clarifies Functionality: Explains how hardware and software work together in a network.
- Easier Troubleshooting: Breaking down the network into layers makes fixing problems easier.
- Standard Terminology: Provides a common language for networking professionals to compare networks.
- Learning New Technologies: Helps users understand new networking technologies as they emerge.
- Understanding Products: Assists in interpreting how networking products work when explained by vendors.
Takeaways
The OSI Model serves as a valuable educational tool for understanding network interactions, the OSI Protocol Suite aimed to implement that model but ultimately did not succeed in gaining traction. In contrast, the TCP/IP protocol suite emerged as the backbone of the Internet, providing a practical and effective set of protocols that facilitated global connectivity. The differences between these models highlight the distinction between theoretical frameworks and practical applications in networking.