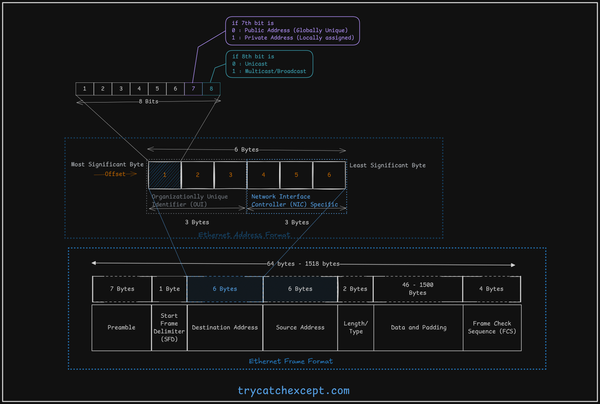
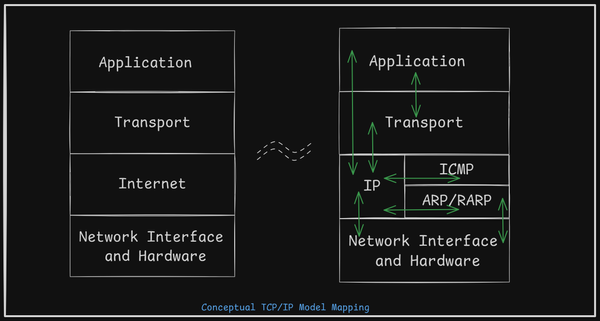
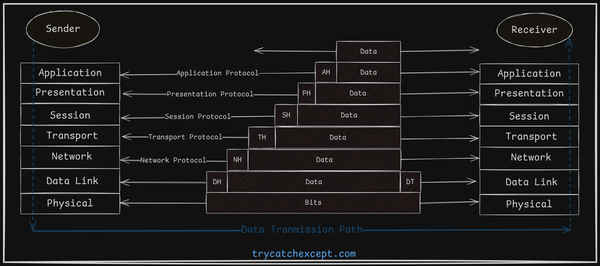
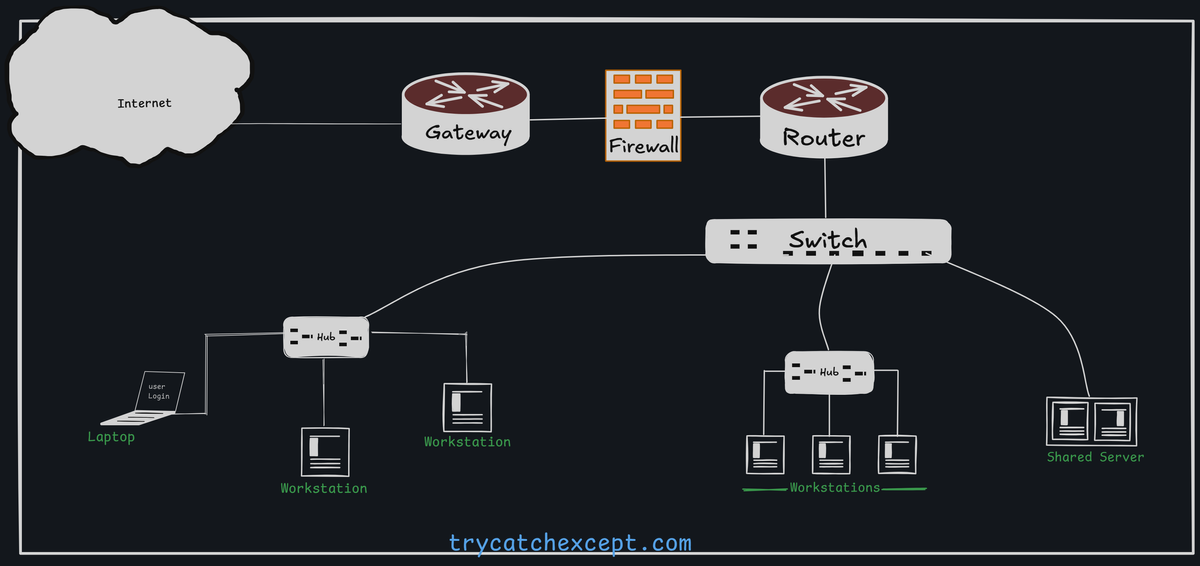
Understanding Computer Network Devices
Network Devices, Repeater, Hub, Bridge, Switch, Router, Gateway, Firewall, Importance of network devices.
Repeater
A repeater is a simple electronic device that takes a weak signal, boosts it, and sends it out stronger. This helps the signal travel longer distances without losing quality. Originally used in telegraphy, repeaters are now common in both phone and data networks.
As data travels over long distances, it can weaken or degrade due to interference, distance, or physical obstacles. Repeaters address this by capturing the weakened signal, boosting it back to its original strength, and retransmitting it, enabling data to travel greater distances without quality loss.
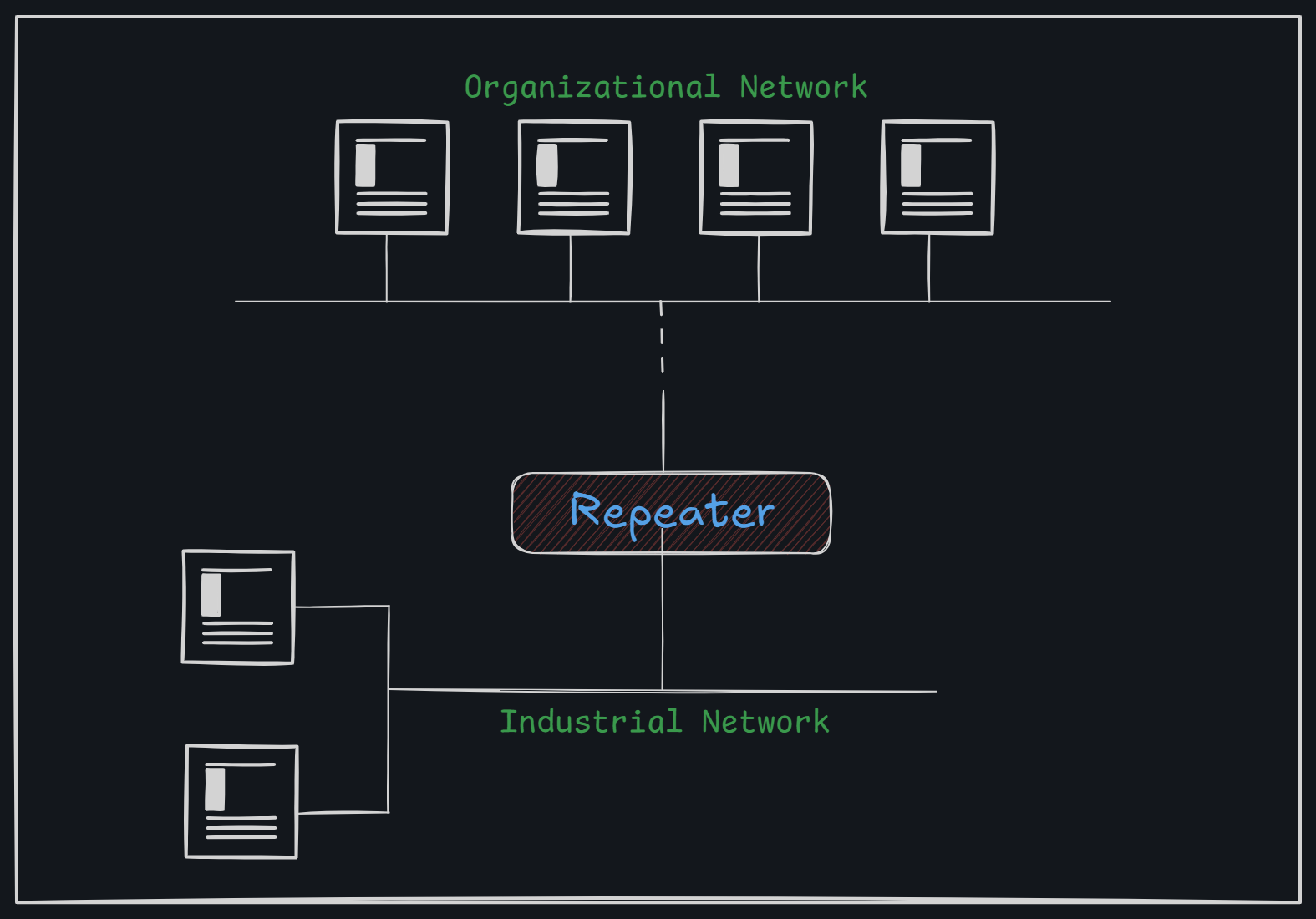
In communications, a repeater can:
- Analog: Boost any signal it receives.
- Digital: Strengthen, reshape, or retime digital signals for a clean re-send.
Since repeaters just boost the physical signal (not the data itself), they work on the Physical layer of the OSI model, which is the first and most basic layer.
Hub
A hub is a basic networking device that connects multiple Ethernet devices (e.g., computers) and operates at the Physical Layer (Layer 1) of the OSI model. Here’s a breakdown:
- Multiport Repeater: Hubs act as multiport repeaters, connecting multiple devices in a single segment.
- Broadcasts Data: Any data packet received at one port is sent to all other ports, creating a shared-medium network.
- Collisions: Only one device can transmit at a time. If multiple devices send data simultaneously, packet collisions occur, slowing down traffic.
- No Traffic Management: Hubs don’t manage data flow or filter traffic, which can impede network efficiency on larger networks.
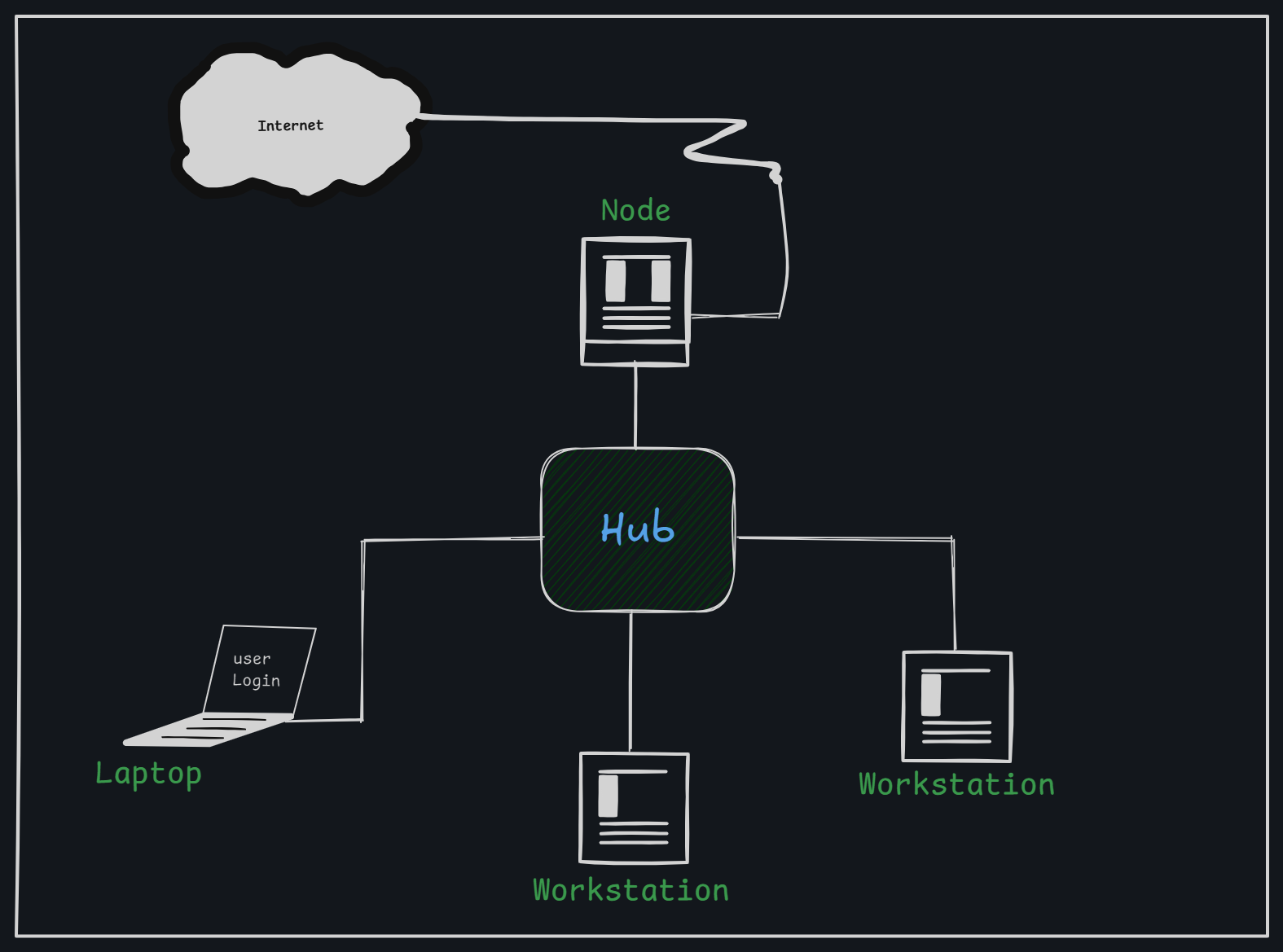
Types of hubs:
-
Passive Hub: This hub acts as a simple connection point for devices. It doesn't boost or clean signals and doesn't require electricity. It's used solely for sharing physical media.
-
Active Hub: An active hub requires power because it amplifies incoming signals before sending them out to other ports. This helps maintain signal strength over longer distances.
-
Intelligent Hub: Also known as smart hubs, these devices function like active hubs but include a microprocessor for added features, like diagnostics. They are more expensive but valuable for troubleshooting.
Bridge
A network bridge connects multiple segments of a network at the data link layer (Layer 2) of the OSI model. Unlike repeaters or hubs that just send signals, a bridge manages network traffic between segments. Bridges use a forwarding database (or bridge table) to keep track of which devices (identified by their MAC addresses) are on which network segments. This table starts off empty and fills up as the bridge receives data. If the bridge doesn't know where to send a frame (data packet), it broadcasts the frame to all segments except the one it came from. This helps it learn where devices are located.
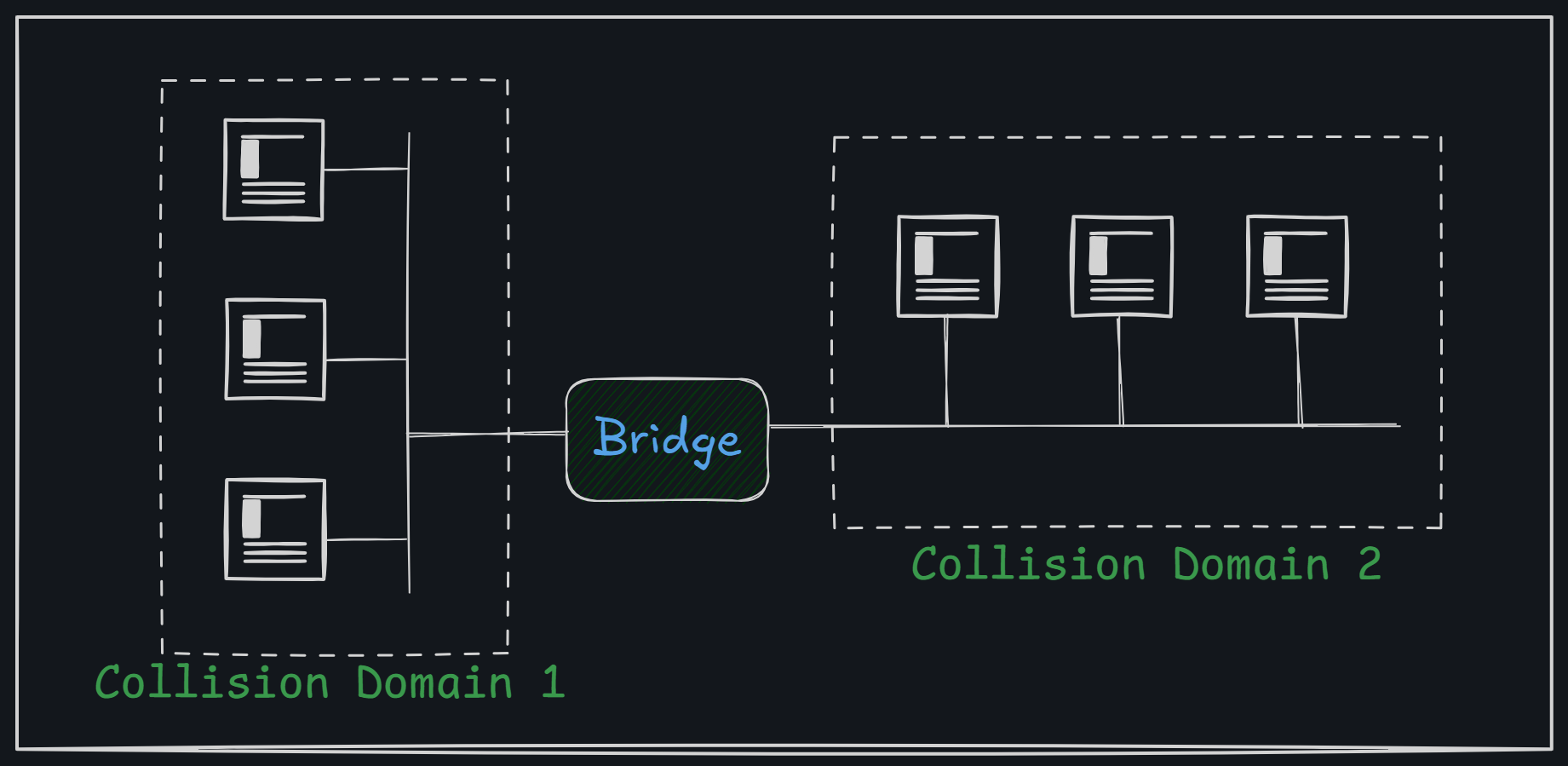
Frame Decision Process:
- Filtering: If the device is on the same segment as the frame, the bridge prevents the frame from going to other segments.
- Forwarding: If the device is on a different segment, the bridge sends the frame to that segment.
- Flooding: If the destination address isn't known, the bridge sends the frame to all segments except the one it was received on.
By managing traffic in this way, bridges help improve network efficiency and reduce unnecessary data collisions.
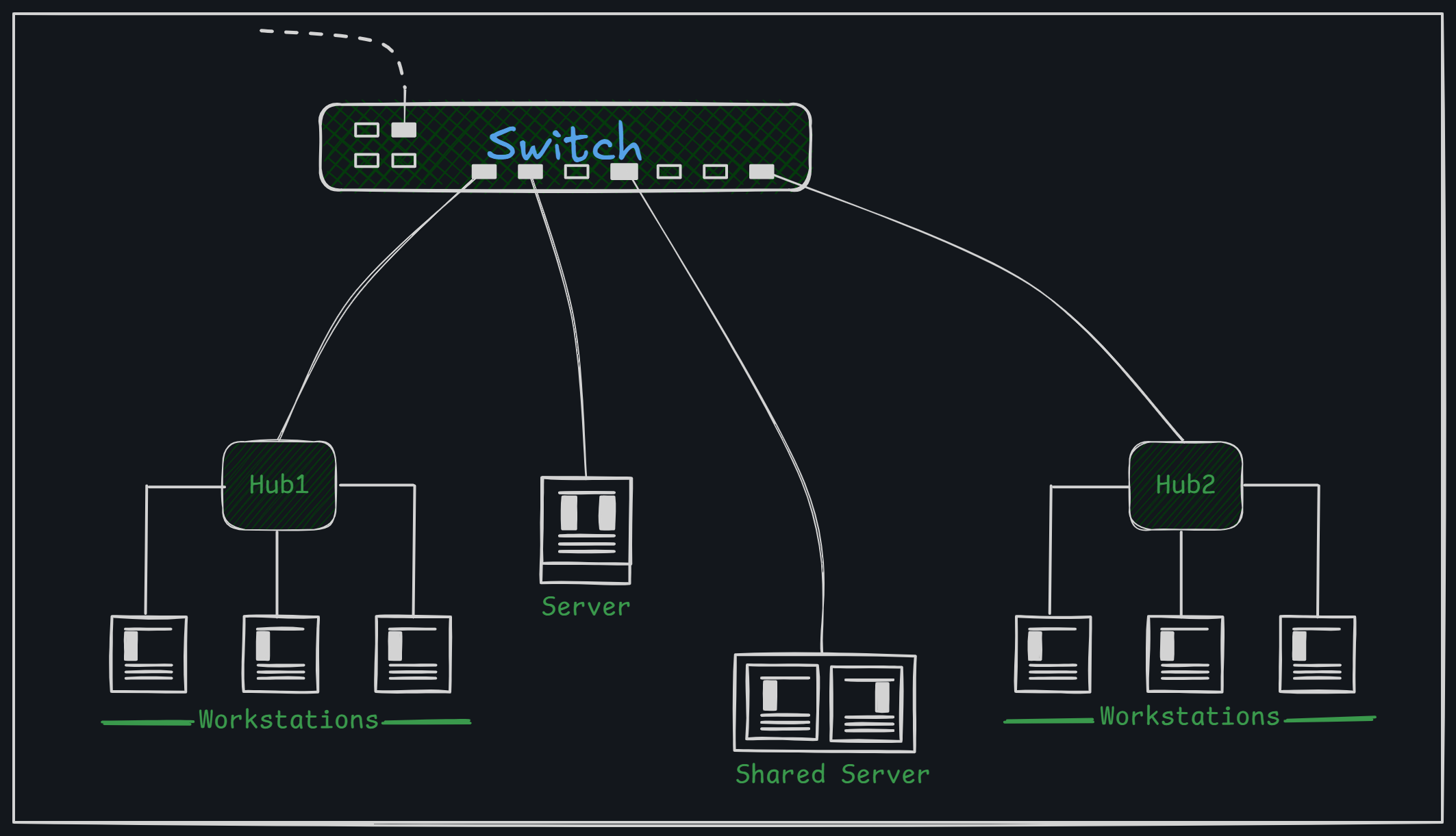
Switch
Low-end network switches look a lot like network hubs but have more features and are a bit more expensive. Unlike hubs, switches can inspect data packets as they arrive. They know where the data is coming from and where it needs to go. Switches send messages only to the specific device they are meant for. This saves network bandwidth and improves performance compared to hubs.
- Speed Options: Most common switches support speeds of 10/100 Mbit/s or 10/100/1000 Mbit/s. Larger switches can even support speeds of 10 Gbit/s.
- How They Work: Switches operate at Layer 2 of the OSI model, using the MAC address from data packets to decide where to send the information.
- Using Advanced Technology: They use special chips called ASICs to create and manage tables that help direct the data.
- Network Benefits: Switches help connect workgroups and reduce network collisions by segmenting traffic effectively.
Four Forwarding Methods of a Layer 2 Switch
- Store and Forward: The switch temporarily holds each data frame and checks it for errors before sending it to the next destination.
- Cut Through: The switch quickly reads the first part of the frame to identify the destination and starts sending it immediately, without checking for errors.
- Fragment Free: This method checks the first 64 bytes of the frame to ensure it has the right address. It combines some benefits of both
Store and ForwardandCut Throughbut leaves error checking for later stages, typically handled by a router. - Adaptive Switching: The switch automatically chooses the best method (from the three above) based on the current network conditions.
Hubs vs. Switches
-
Hub: A basic device that sends incoming data to all ports, like a loudspeaker announcing a message to everyone. This can cause data collisions, making the network slower and less efficient.
-
Switch: A smarter device that directs incoming data only to the specific port where the intended device is located. If it doesn’t know the correct port, it sends the data to all other ports except the one it came from. This targeted approach significantly improves network performance by reducing unnecessary traffic.
Router
A router is a device used in computer networks that helps send data packets from one place to another. It does this by "routing" the packets toward their destinations. Routers work at Layer 3 of the OSI model, known as the Network layer. This is where Internet Protocol (IP) addresses are used to manage data traffic.
How routing fits into the OSI Model?
-
OSI Model Overview: The OSI model is a framework that helps us understand how different network protocols and devices interact. It has seven layers, but we mainly focus on Layers 2 and 3 for routing.
-
Layer 2 (Data Link Layer): This layer deals with Ethernet protocols and MAC addresses. Devices like switches operate at this level.
-
Layer 3 (Network Layer): This layer uses IP addresses to route data.
Routersare the main devices at this layer, helping data travel between different networks.
How Routers Utilize Ethernet MAC and IP Addresses
In Layer 3, we have the IP protocol and IP addresses. Nowadays, nearly all networking relies on Ethernet and IP. This means that, typically, each packet on your network carries both a source and destination Ethernet MAC address, along with a source and destination IP address. Remember this as a key point.
What a router does with your network traffic:
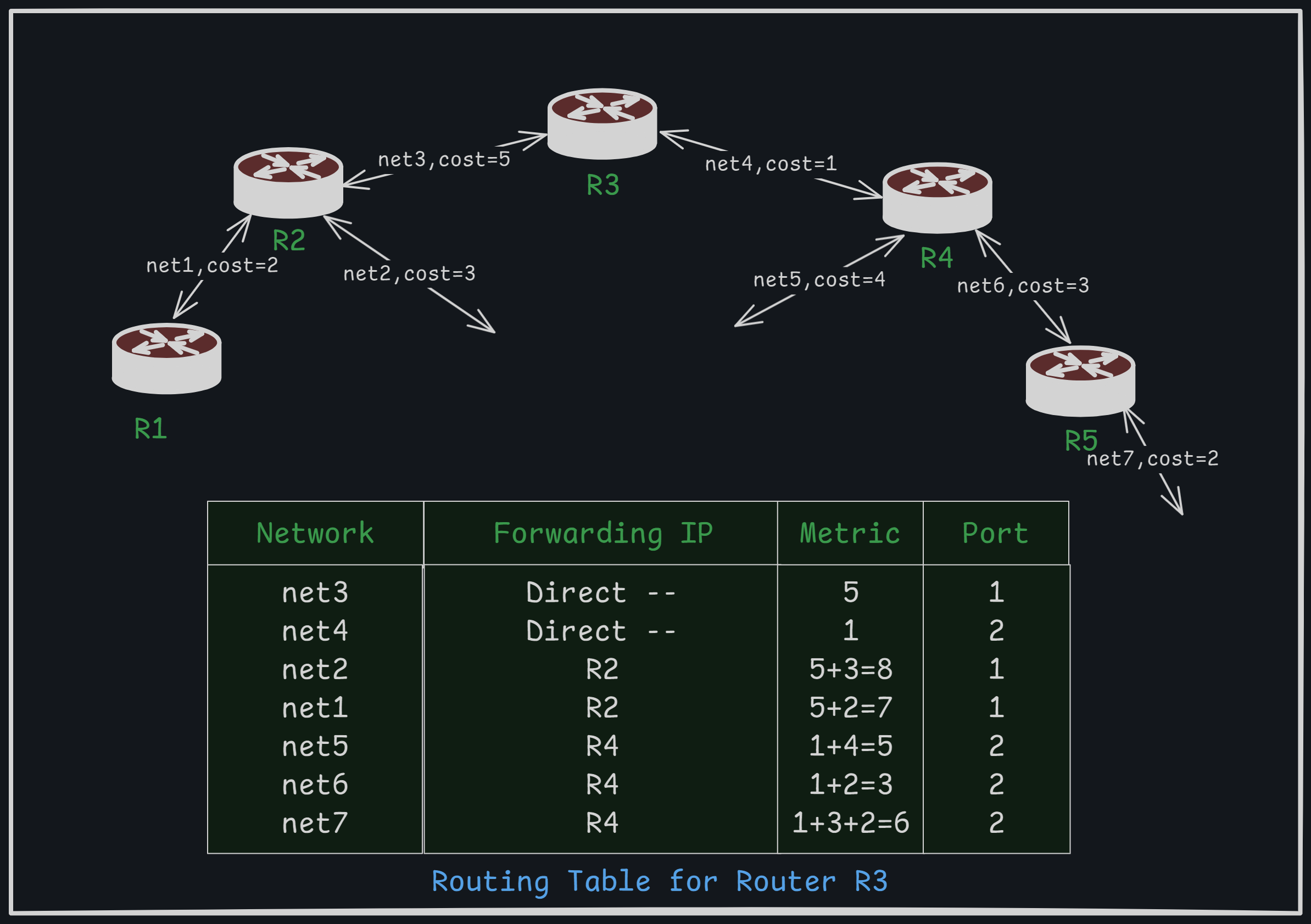
Routers work with both Ethernet and IP addresses but mainly focus on the destination IP address of the packet. When a packet reaches the router, it checks the destination IP address and searches for it in its routing table to decide where to send it next.
For example: In the picture above, the routing table for router R3 is shown. If a packet needs to be forwarded to some system on Network 7 (net7), the router will look up the destination address in the packet and compare it with the entries in the routing table. From the table, it finds that it can reach net7 by forwarding the packet to Router R4, which can be reached by sending the packet on port 2. Router R4 will, in turn, forward the packet toward net7 by forwarding it on port 2, toward router R5.
Routers learn routes either manually (static) or through routing protocols (dynamic) and use these to find the best path for traffic. Often, a "default route" (also called the "gateway of last resort") is set up as a fallback for cases where no specific route exists. For most home users with a single Internet connection, all traffic goes through this default route to their ISP. ISPs, however, have multiple options and choose the best route from hundreds of thousands in milliseconds. As data travels across the Internet, it may pass through many routers; if no route is available, the router discards the data and sends an ICMP destination unreachable message back.
Router Actions Before Sending Traffic
-
Perform Network Address Translation (NAT):
-
NATisn’t a traditional role of a router, but many modern routers, especially those in homes and small businesses, are equipped to handle it. In fact, these routers often work as "all-in-one" devices, combining routing, NAT, and firewall functions. For larger companies, dedicated firewalls may also handle NAT. -
With NAT, the router takes your private IP address—used only within your internal network—and translates it to a public IP address before sending data out to the internet. This allows multiple devices on your local network to share a single public IP address while keeping internal IP addresses hidden from outside networks.
-
-
Replace source MAC address with the router's MAC address:
- The
ARPprotocol is used to connect your computer's source MAC address to your IP address. - The
ARPprotocol is a broadcast-oriented protocol, and routers discard broadcasts. This means that ARP doesn't work through routers. Because of this, the router must replace your source MAC address with the router's MAC address. The router also adds the destination host or next-hop router's MAC address to the data link header.
- The
-
Encapsulate the packet for the protocol of the WAN:
- When sending data across different types of networks, routers often need to convert data to match the protocol of the outgoing network. This process is called
encapsulation. - For example, if a router connects to the internet via a PPP (Point-to-Point Protocol) link and to the local network (LAN) using Ethernet, it needs to handle data differently for each network type. When data arrives in an Ethernet format, the router removes the Ethernet "wrapper" (or
de-encapsulatesit), modifies it as needed, and then repackages (orre-encapsulates) it for PPP before sending it across the internet. This conversion allows the router to bridge networks that use different protocols seamlessly.
- When sending data across different types of networks, routers often need to convert data to match the protocol of the outgoing network. This process is called
-
Fragmentation:
- Routers connect different networks, each of which may have a unique limit on the size of data it can handle, known as the
Maximum Transmission Unit (MTU). If a large packet of data needs to pass through a network with a smaller MTU, the router breaks it into smaller, manageable parts, a process called fragmentation. This ensures that even large data packets can travel across networks with lower size limits without any loss. - When these smaller fragments reach the destination network, the receiving router or device reassembles them back into the original packet, making it seamless for each side of the communication. This fragmentation and reassembly process happens for every data packet and response, allowing smooth and efficient communication across networks with varying MTU capacities.
- Routers connect different networks, each of which may have a unique limit on the size of data it can handle, known as the
Gateways
A gateway, in computer networking technology, is a node that serves as an entrance to another network, and vice-versa. Gateways are most commonly used to transfer data between private networks and the internet. They can perform the operations of routing, fragmentation and translation. A gateway is an essentially a router, although other devices (such as any PC or server) can function as a gateway.
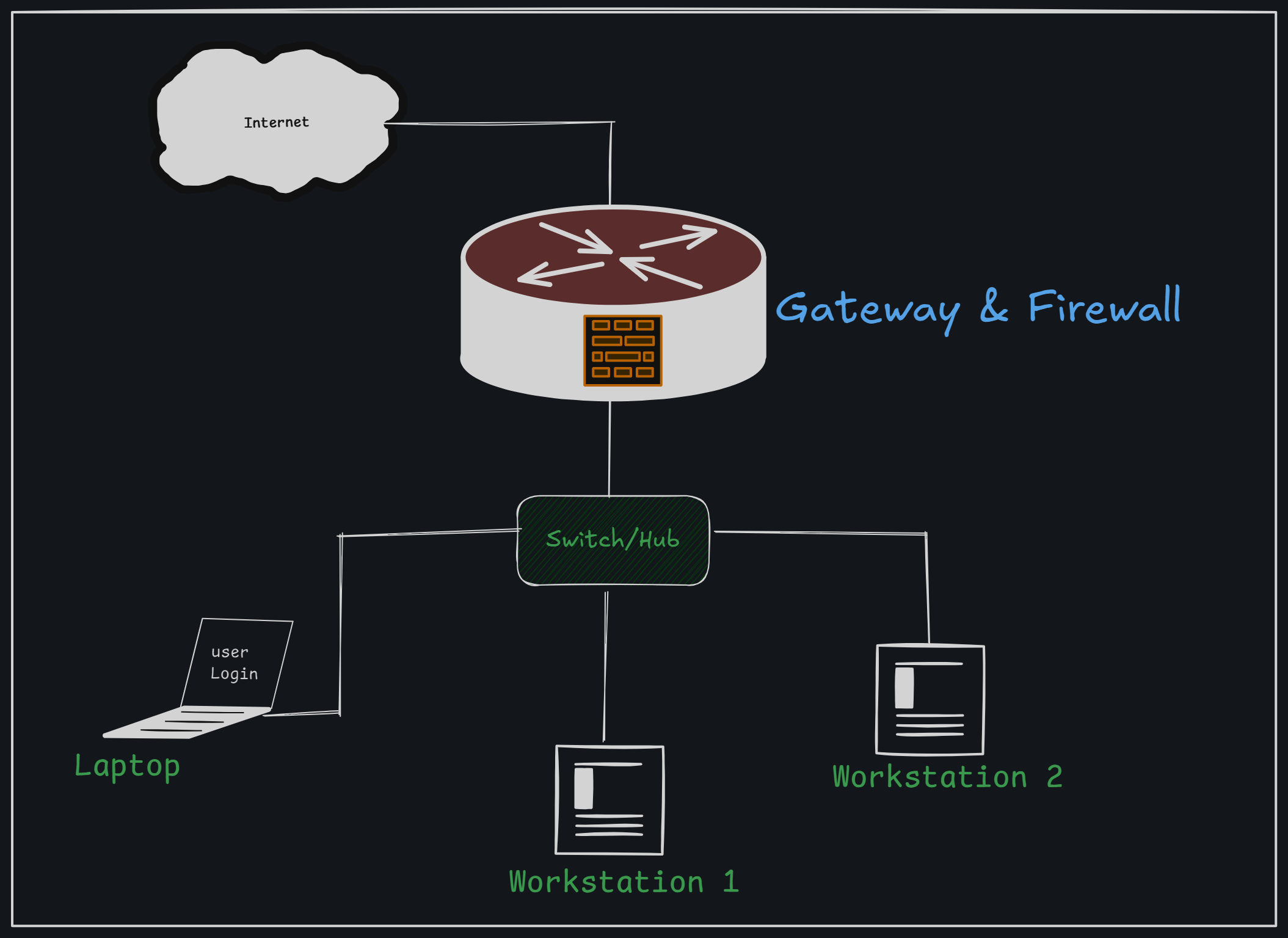
Firewall
A firewall is a network device that monitors and controls incoming and outgoing network traffic based on predetermined security rules. It can be hardware-based, software-based, or a combination of both. Firewalls are essential components of any network, whether it's a home network, a corporate environment, or a data center.
Role of Firewalls in the Internet
-
Traffic Control: Firewalls determine which data packets are allowed to enter or leave the network based on predefined rules. This helps to regulate traffic and prevent unauthorized access to sensitive information.
-
Protection from Attacks: Firewalls defend against various types of attacks, such as denial-of-service (DoS) attacks, malware, and intrusions. By blocking suspicious traffic, they help maintain the integrity and availability of the network.
-
Network Segmentation: Firewalls can segment a network into different zones, allowing organizations to create secure environments for sensitive data. This reduces the attack surface by limiting access to critical resources.
-
Policy Enforcement: Organizations can enforce security policies through firewalls, ensuring that only authorized users and devices can access specific resources. This is especially important in corporate environments where sensitive information needs protection.
-
Monitoring and Logging: Firewalls keep logs of traffic patterns and potential security incidents, allowing network administrators to monitor activities and analyze threats. This data is invaluable for incident response and compliance audits.
-
Support for Virtual Private Networks (VPNs): Firewalls often support VPN connections, enabling secure remote access to the internal network for employees working from home or other remote locations.
Why is a Firewall needed?
-
Protection Against Unauthorized Access: Without a firewall, networks are vulnerable to intrusions from cybercriminals and malicious software. Firewalls help prevent unauthorized users from accessing sensitive data.
-
Defense Against Malware: Firewalls can detect and block malicious traffic, such as viruses and worms, protecting devices and data from infections.
-
Control Over Network Traffic: Firewalls allow organizations to control and manage traffic flows, ensuring that only legitimate traffic is permitted while blocking potentially harmful connections.
-
Compliance Requirements: Many industries are subject to regulations that require the implementation of security measures, including firewalls. They help organizations meet these compliance standards.
-
Peace environment: Knowing that a firewall is in place provides peace of mind to users and organizations, assuring them that there are protective measures against cyber threats.
Takeaways
Network devices are essential for connecting and managing traffic between computers and networks. They enable data to move seamlessly across local and global networks, from small home setups to large enterprise systems.
Different devices serve different roles:
Routersdirect traffic across networks, often using routing tables to choose the best path.Switchesoperate within networks, connecting devices and handling data at high speeds.Firewallsprovide security, controlling data flow based on predefined security rules.